Manage secrets
Use Secrets to manage values that are encrypted and hidden from users, but can still be read and used by API Monitoring test scripts. The Secrets feature for API Monitoring Tests requires a qualifying plan; check your plan or contact Sales to get started.
How secret management Works
The Secrets feature allows API Monitoring team owners and administrators to create and manage variables with a key/value pair, where the value is encrypted and hidden, and allows all team members to use the variables in their tests with the new built-in function {{get_secret(key)}}.
In the same way you might have a .env or config file in your app that includes sensitive variables you don't want to be checked in to your project's version control repository. The Secrets feature can help you keep sensitive information secure.
Examples
Some common cases where secrets can be used:
- You might have an API key or access token that you do not wish to be visible in your tests for security reasons.
- You are working with an API that requires authentication credentials that you don't want exposed.
- You don't want to send certain information to third-party integrations.
This article covers the following topics:
- Manage secrets
- Create secrets at the team Level
- Create secrets at the bucket Level
- Use secrets in tests
Manage secrets
As a team owner or admin, you can and manage secrets at the team level and at the bucket level. Secrets created at the team level can be used by all tests in all buckets. Secrets created at the bucket level can be used only by tests within that bucket.
To manage secrets at the team level, see:
To manage secrets at the bucket level, see:
Secrets have a 4096-character limit.
Create secrets at the team level
As an API Monitoring team owner or admin, you can create secrets at the team level.
Follow these steps:
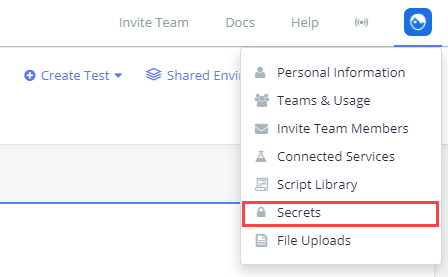
- Go to the API Monitoring tab.
- Click your profile on the top-right and select Secrets from the dropdown list:
- On the Secrets page, click Add Secret.
A new secret key/value pair is created. - Enter the name that will be used to access the secret throughout your tests.
- Enter the value.
- Click Save Changes.
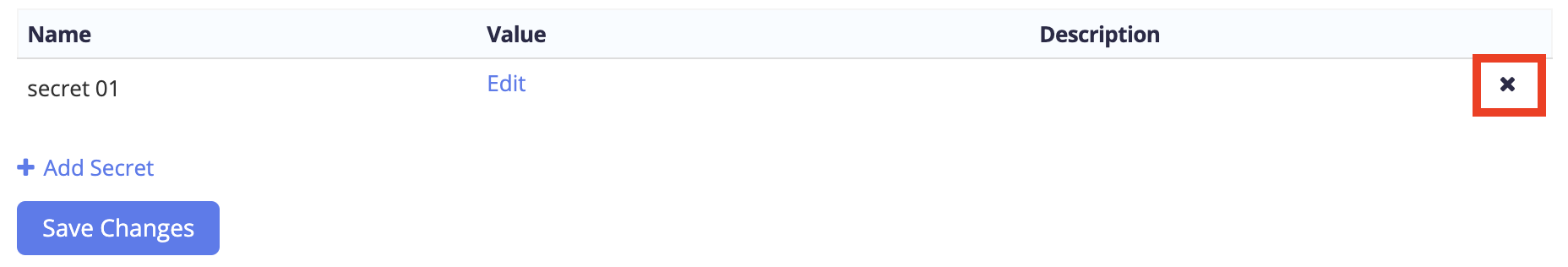
Edit and delete secrets at the team level
To edit an existing secret, go to the Secrets page and click Edit next to the secret you wish to change the value for. Enter the new value and click Save Changes.
To delete a secret, go to the Secrets page and click the x next to the secret that you wish to delete.
Create secrets at the bucket level
You can create secrets at the bucket level if you have appropriate RBAC privileges. If you don’t have permission to create secrets, contact your team owner or administrator.
Follow these steps:
- In API Monitoring, click Bucket Settings in the top right corner.
The Bucket Settings page opens. - Scroll down to the Bucket Secrets section.
- Click Add Secret.Secrets on a bucket level can’t have the same name as secrets on the team level.
- Enter the Name and Value. Description is optional.
Click Save Changes.
Edit and delete secrets at the bucket level
To edit an existing secret, go to the Bucket Settings page and scroll down to the Bucket Secrets section. Click Edit next to the secret that you wish to change the value for. Enter the new value, and click Save Changes.
To delete a secret, click the x next to the secret that you wish to delete.
Team owners and admins can create roles with various permissions, for example, the View or Manage Bucket Permissions, and assign the roles to team members. For more information, see Role-based access control.
Use secrets in tests
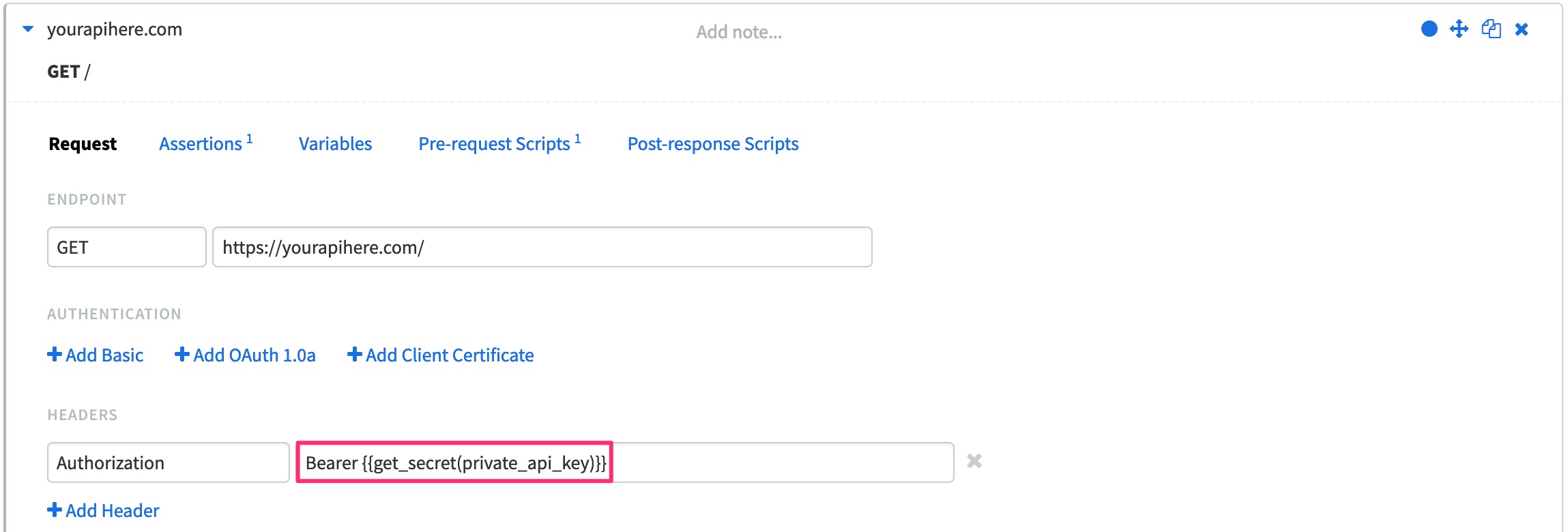
To use secrets in your tests, you'll have to use a built-in function:
| Variable/Function | Description |
{{get_secret(key)}}
|
Retrieves the secret value for the key name. |
To see what team level secrets are available in your BlazeMeter API Monitoring account, you'll need to check with your team owner which can be found in the Team members page. To see what secrets are available at the bucket level, go to the Bucket Settings page.
This built-in function can be used just like any other BlazeMeter API Monitoring built-in functions, which means you can add it to your environment settings, initial variables, pre-request/post-response scripts, etc. To use it in scripts, make sure you're calling the function as get_secret(key) without the parenthesis:
// Example pre-request / post-response script
request.params.push({name:"api_key", value: get_secret("secret_key")});
Whenever you have a step in your API tests that's using the get_secret function or is referencing a variable that was set using this function, the results for that step will omit any information that might contain the value for that secret, including the headers and body for both request and response. This also applies to any step that has a pre-request script or post-response script as it might reveal the value of the secret value.