Manage sensitive data securely with secrets
Secrets are objects that contain sensitive data, such as passwords, tokens, credit card numbers, or any other data that shouldn't be exposed. By using secrets, you do not have to hard code any sensitive data into your test scripts. When you run a test, whenever an enabled secret appears in reports or logs during and after run time, the value of the secret is replaced with asterisks (*).
To use secrets, you need to create them in your Workspace settings. For more information on how to create secrets in your workspace, see Create and Manage secrets.
If your test scenarios require the use of secrets, such as API keys, token, or credentials, be sure that:
- only production and non-sensitive secrets are used.
- all secrets are strictly limited in scope and privilege, and access only test-specific resources or data.
- secrets should be temporary and rotated regularly.
- you avoid the use of secrets that provide access to productions environments or sensitive customer data.
Use secrets to your test script
Once you created the secrets in your workspace, you can use them in your test script.
Use secrets in JMeter
In JMeter, you can reference a configured secret using the prefix BZM_SECRET. Add a default value to your secret after the secret name. If the secret is not configured in your workspace, the test uses the default value.
${__P(BZM_SECRET_secret1,DefaultValue)}Secrets included in your test script are automatically detected when you upload your test script when your test script is written in JMeter. The Secrets section appears as enabled, but is read only.
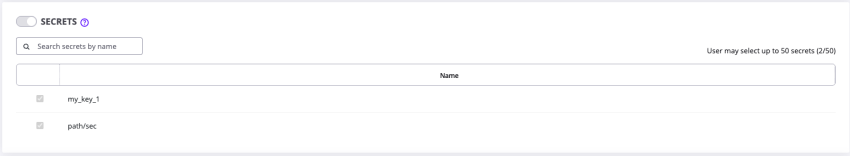
If no secrets are detected in your JMeter script, you can manually choose which secrets to include.
Use secrets in a JMeter script that references other scripts
You can use secrets in your JMeter test script that reference other scripts. The following examples show a script that references a Python script.
execution:
- executor: locust
concurrency: 10
locations:
us-east4-a: 1
ramp-up: 1m
hold-for: 5m
scenario: load_test
secrets:
- secret1
scenarios:
load_test:
script: secrets_locust.pyPython script with secrets
import os
from locust import HttpUser, task, between
class LoadTest(HttpUser):
host = "https://blazedemo.com"
wait_time = between(1, 3)
def on_start(self):
self.base_url = "https://blazedemo.com"
self.endpoints = ["/login"]
self.secret = os.getenv("BZM_SECRET_secret1", "value")
self.endpoints.append(f"/echo.php?echo={self.secret}")
@task
def perform_requests(self):
for endpoint in self.endpoints:
self.client.get(endpoint)Manually enable secrets
You can manually enable secrets when:
-
using executors other than JMeter. Because BlazeMeter cannot automatically detect secrets that are not written in JMeter, you need to configure the secrets in your workspace settings and then enable them manually.
-
you want to enable Secrets due to the possibility of sensitive data showing in test results or logs. Any selected secrets that appear in your test results or logs are replaces with asterisks (*).
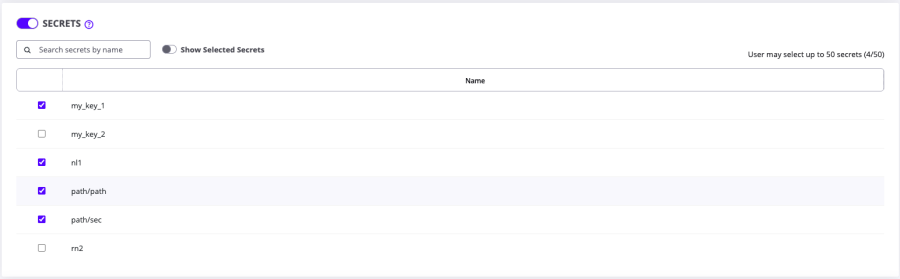
To enable the Secrets section and choose which configured secrets to include in your test:
-
On the test configuration page, scroll to the Secrets section and toggle the button ON.
-
Select all relevant secrets for your test script. Search for secrets using the search bar. To only show the secrets you have already selected, click Show Selected Secrets.